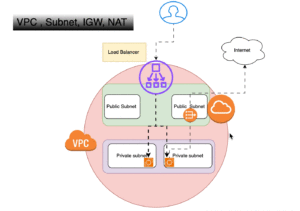
Infrastructure as Code (IaC) revolutionizes the traditional approach to infrastructure management by treating infrastructure provisioning and configuration as code. This means that instead of manually configuring servers, networks, and other infrastructure components, developers and operations teams use code to define and automate these processes. This approach offers numerous benefits, including increased efficiency, consistency, scalability, and most importantly, enhanced security.
Security Benefits of Infrastructure as Code
Consistency: With IaC, infrastructure configurations are codified and version-controlled. This ensures consistency across environments, reducing the likelihood of configuration drifts that could lead to security vulnerabilities.
Repeatability: Infrastructure deployments can be automated and repeated consistently across multiple environments, reducing human errors and ensuring that security configurations are consistently applied.
Audibility and Accountability: Infrastructure changes made through code are logged and version-controlled, providing a clear audit trail of who made changes and when. This enhances accountability and makes it easier to trace security-related changes.
Security by Design: Security best practices can be embedded into infrastructure code from the outset. For example, encryption can be automatically enabled, access controls can be defined, and security patches can be applied consistently.
Reduced Attack Surface: By automating the provisioning and configuration of infrastructure, IaC minimizes the attack surface by reducing the number of manual configurations and potential misconfigurations that could be exploited by attackers.
Faster Remediation: In the event of security vulnerabilities or incidents, IaC allows for rapid remediation by updating the codebase and reapplying the changes across environments, ensuring that security patches are applied quickly and consistently.
Implementing Security Best Practices in IaC
Secure Coding Practices: Adhere to secure coding practices when writing infrastructure code, such as avoiding hard-coded secrets and credentials, using parameterization for sensitive data, and validating inputs to prevent injection attacks.
Least Privilege Principle: Follow the principle of least privilege when defining access controls in infrastructure code, ensuring that only necessary permissions are granted to users and resources.
Security Testing: Include security testing as part of the CI/CD pipeline for infrastructure code, including static code analysis, vulnerability scanning, and compliance checks to identify and remediate security issues early in the development lifecycle.
Hardening Templates: Utilize hardened templates and configurations provided by cloud service providers or security frameworks to ensure that infrastructure deployments adhere to security best practices by default.
Secrets Management: Use secure secrets management solutions, such as Azure Key Vault, to store and manage sensitive information such as passwords, API keys, and certificates securely, and integrate them into infrastructure code as needed.
Continuous Monitoring and Compliance: Implement continuous monitoring and compliance checks for infrastructure deployments using tools like Azure Security Center or third-party solutions to detect security threats, misconfigurations, and compliance violations in real-time.
By implementing security best practices in Infrastructure as Code, organizations can effectively mitigate security risks, improve compliance, and enhance the overall security posture of their cloud environments.