Ansible Zero to Hero — Ansible Framework for Azure Pipelines to Execute on the Remote Machines — Part 5
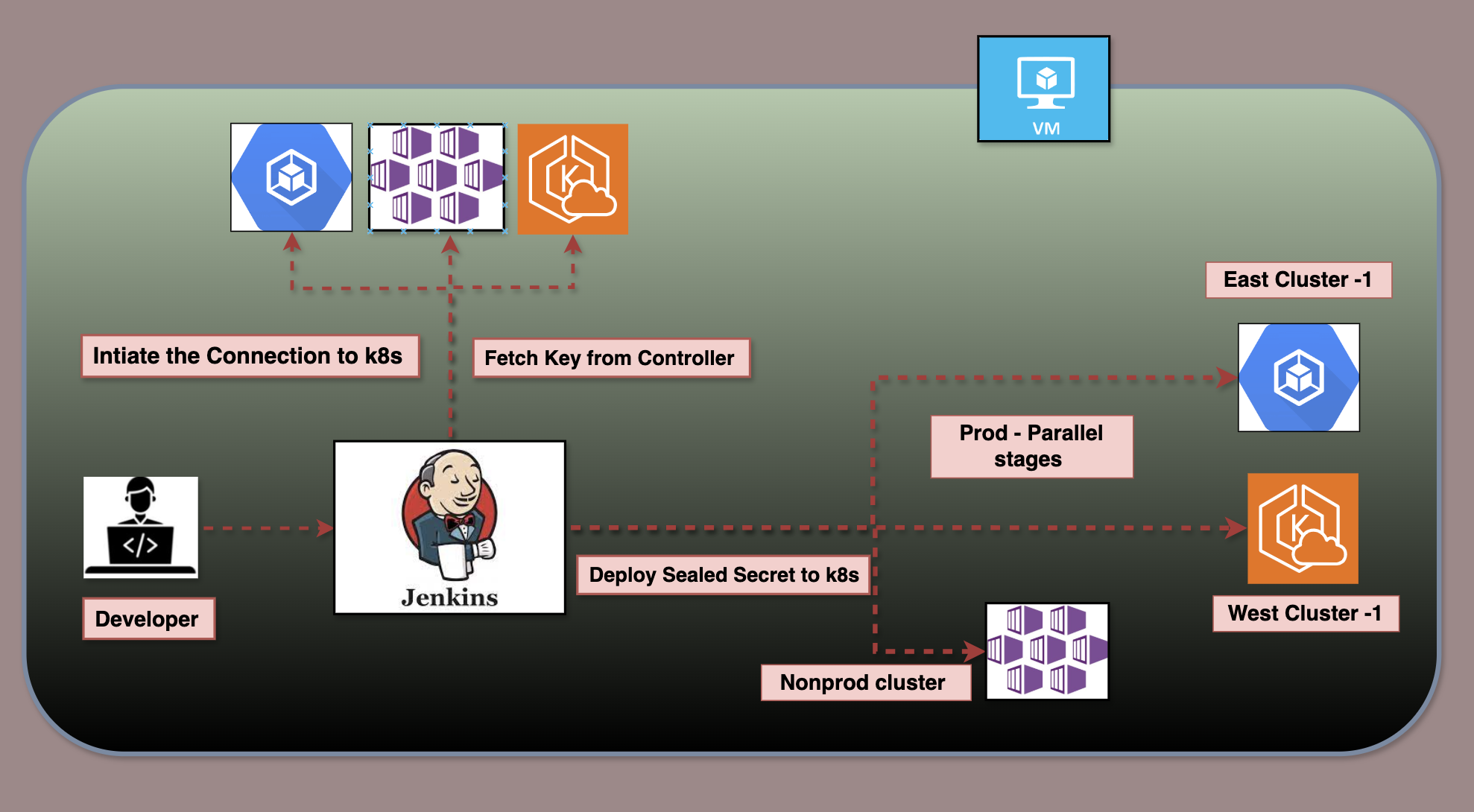
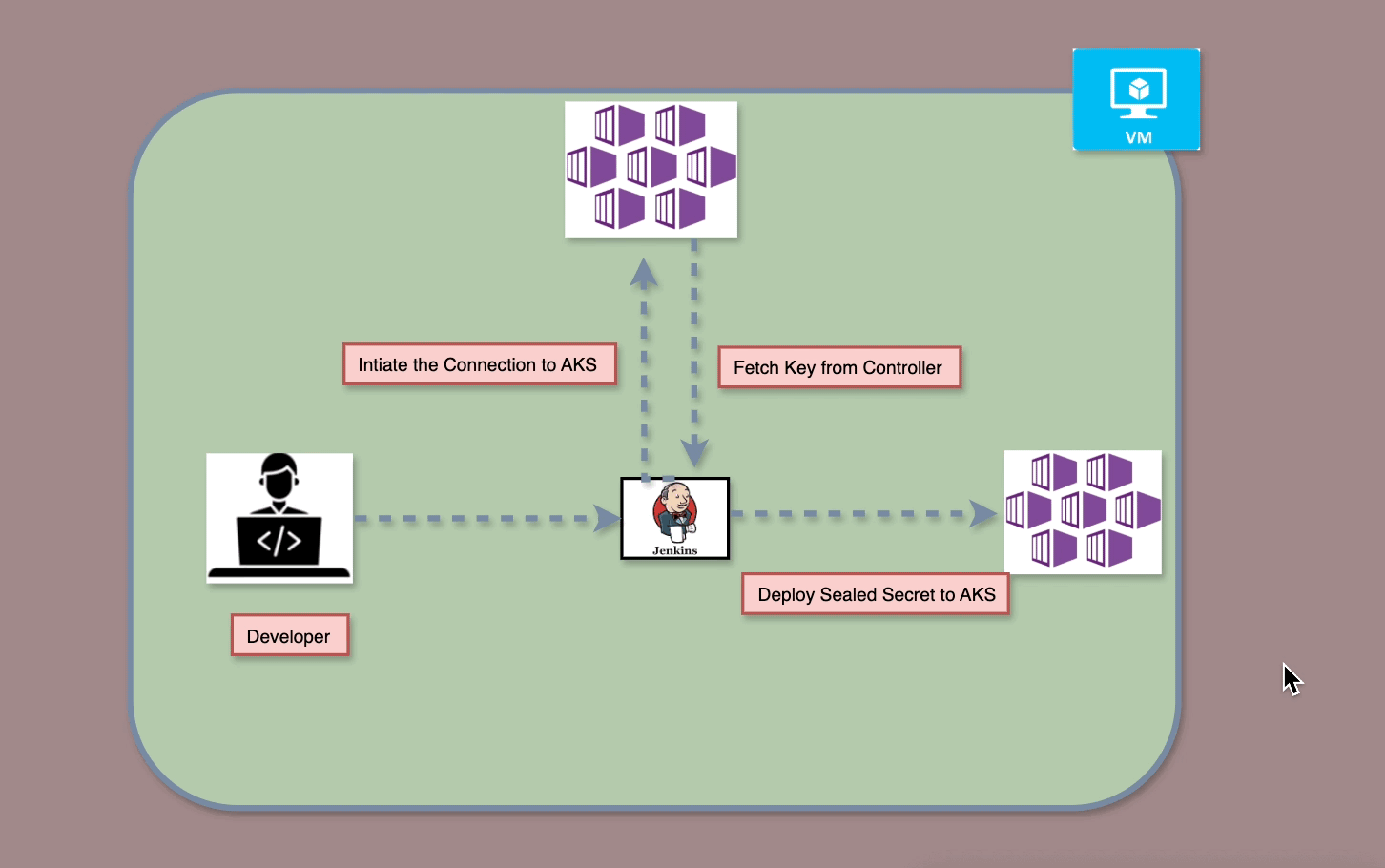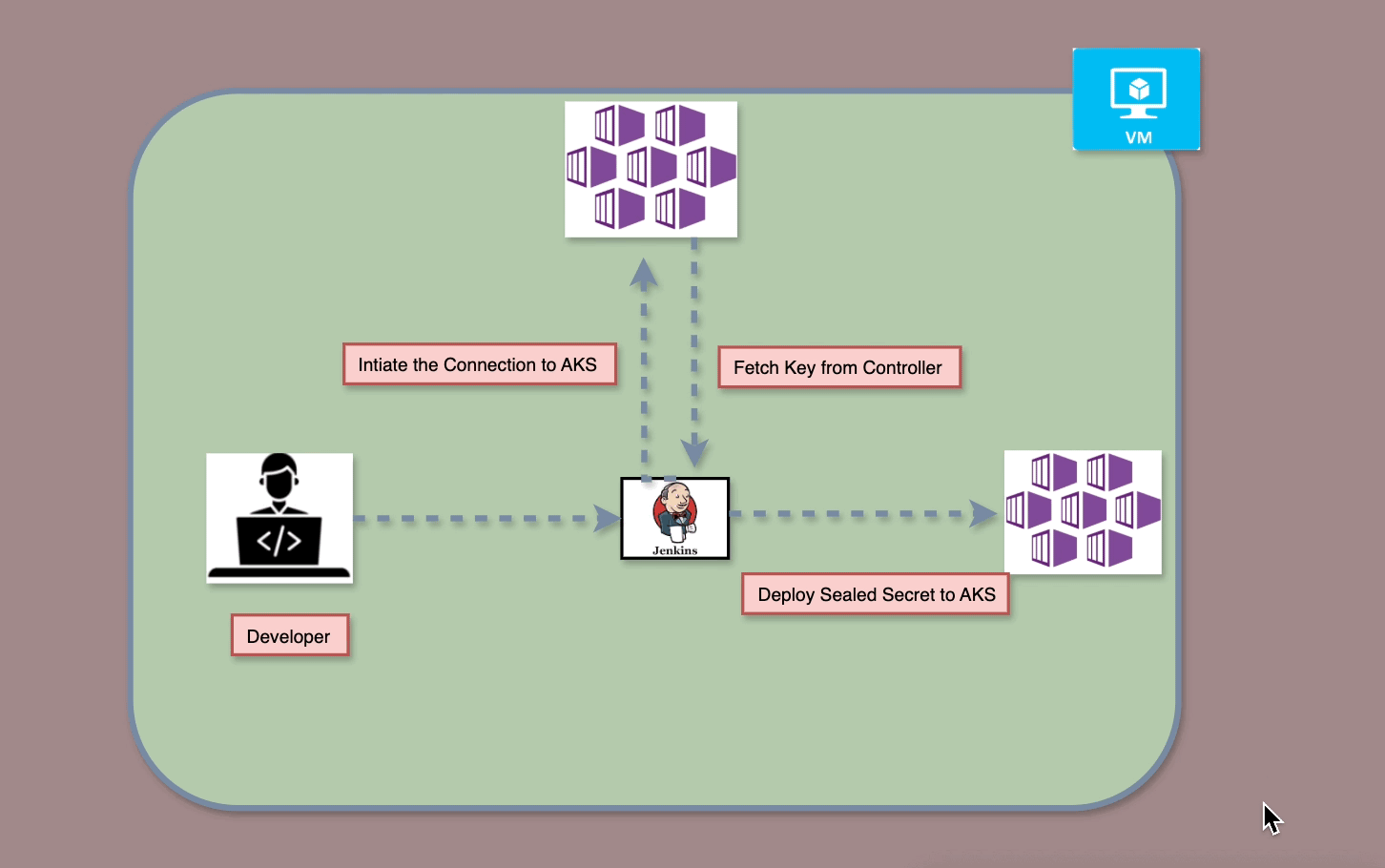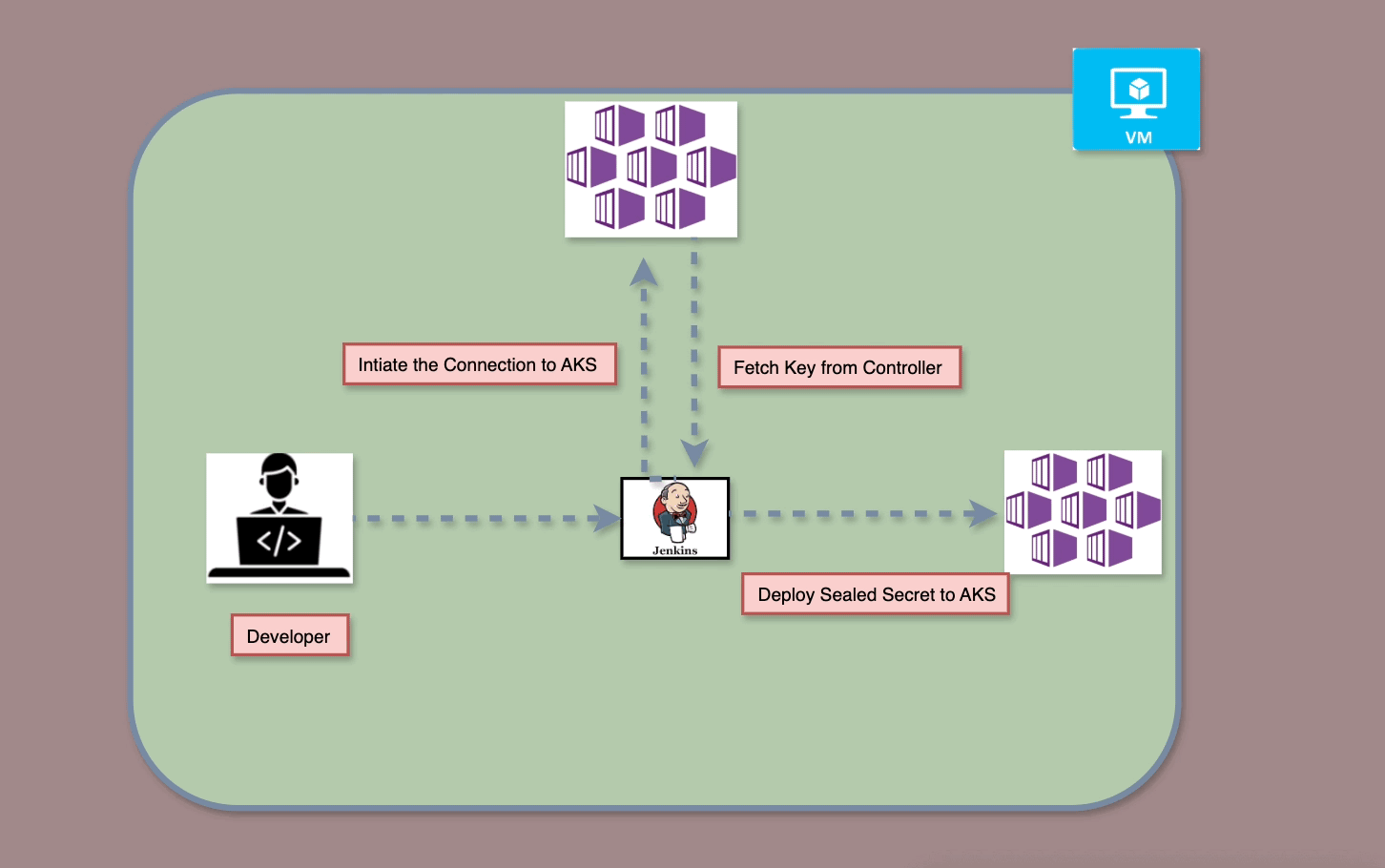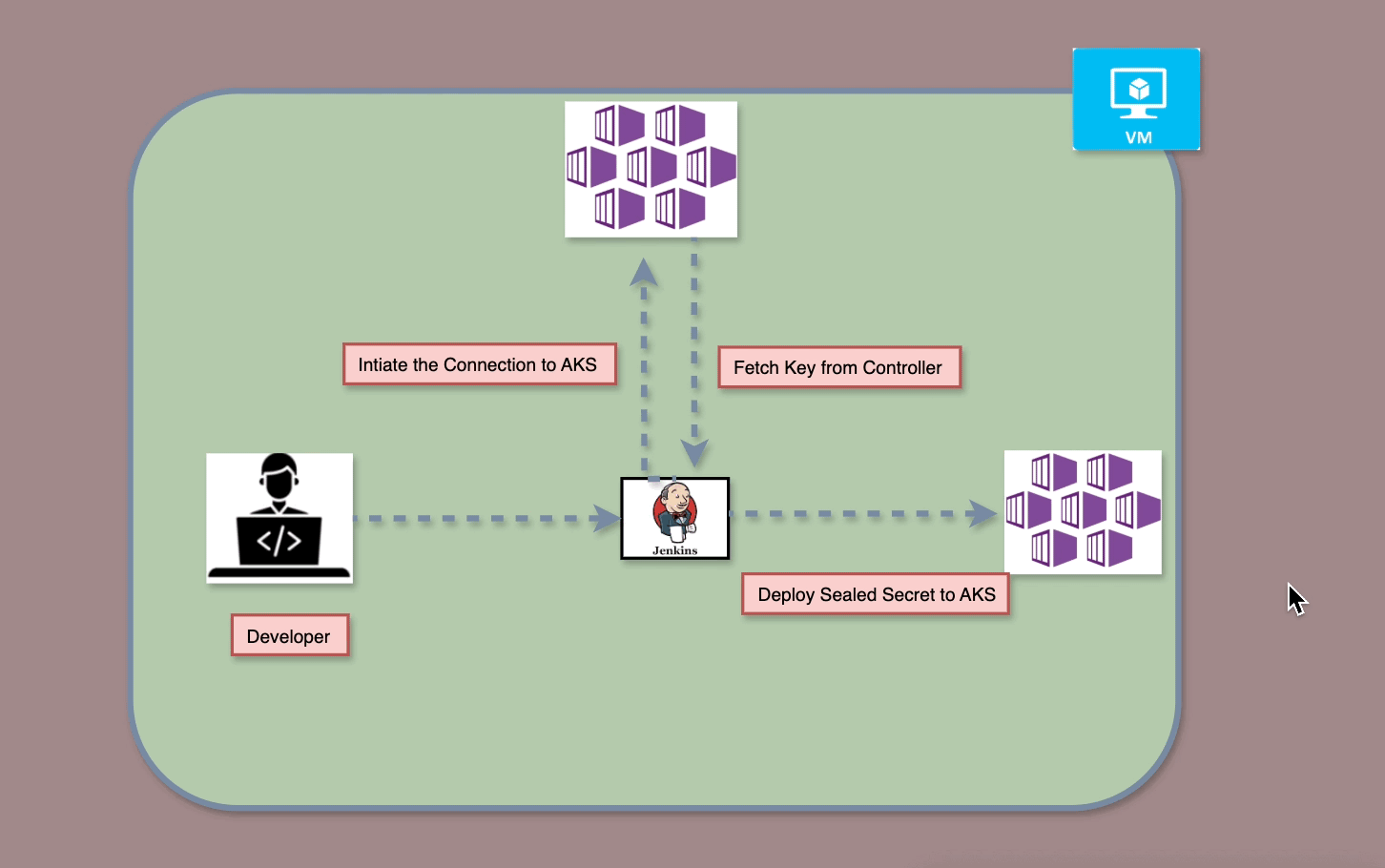
This guide explains integrating Ansible with Azure Pipelines for automated infrastructure deployment. It covers configuring inventory, group variables, roles, and a master playbook for centralized execution. The pipeline includes validation and approval stages before applying Ansible playbooks. This approach ensures efficient, reliable, and consistent CI/CD for infrastructure automation.