Infra Automation by Terraform -AKS Provisioning & RBAC for AD Group — Part9
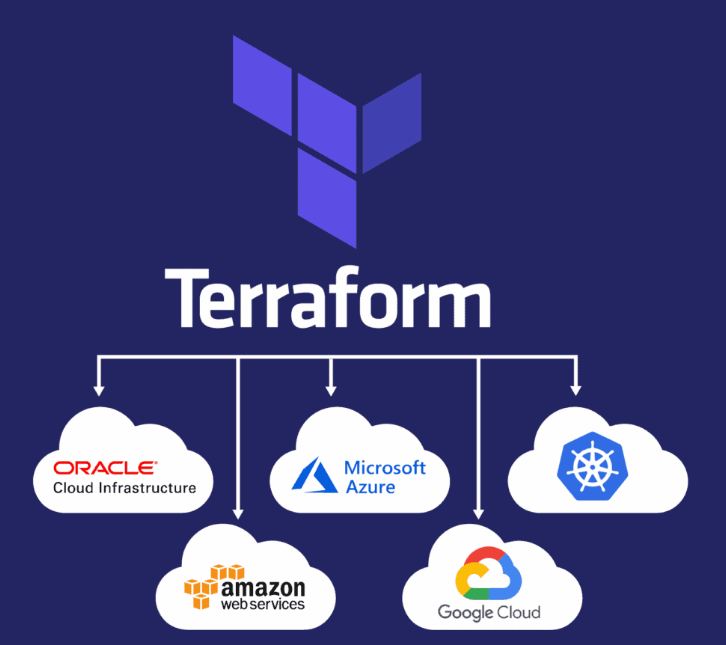
Azure Kubernetes Service (AKS) simplifies the deployment and management of containerized applications with Kubernetes. Integrating Azure Role-Based Access Control (RBAC) with AKS enhances security by controlling user access within the Kubernetes environment. By provisioning a service principal and adding it to an Azure Active Directory (AD) group, administrators can efficiently manage permissions. This setup ensures that only authorized users and applications can access and modify resources.