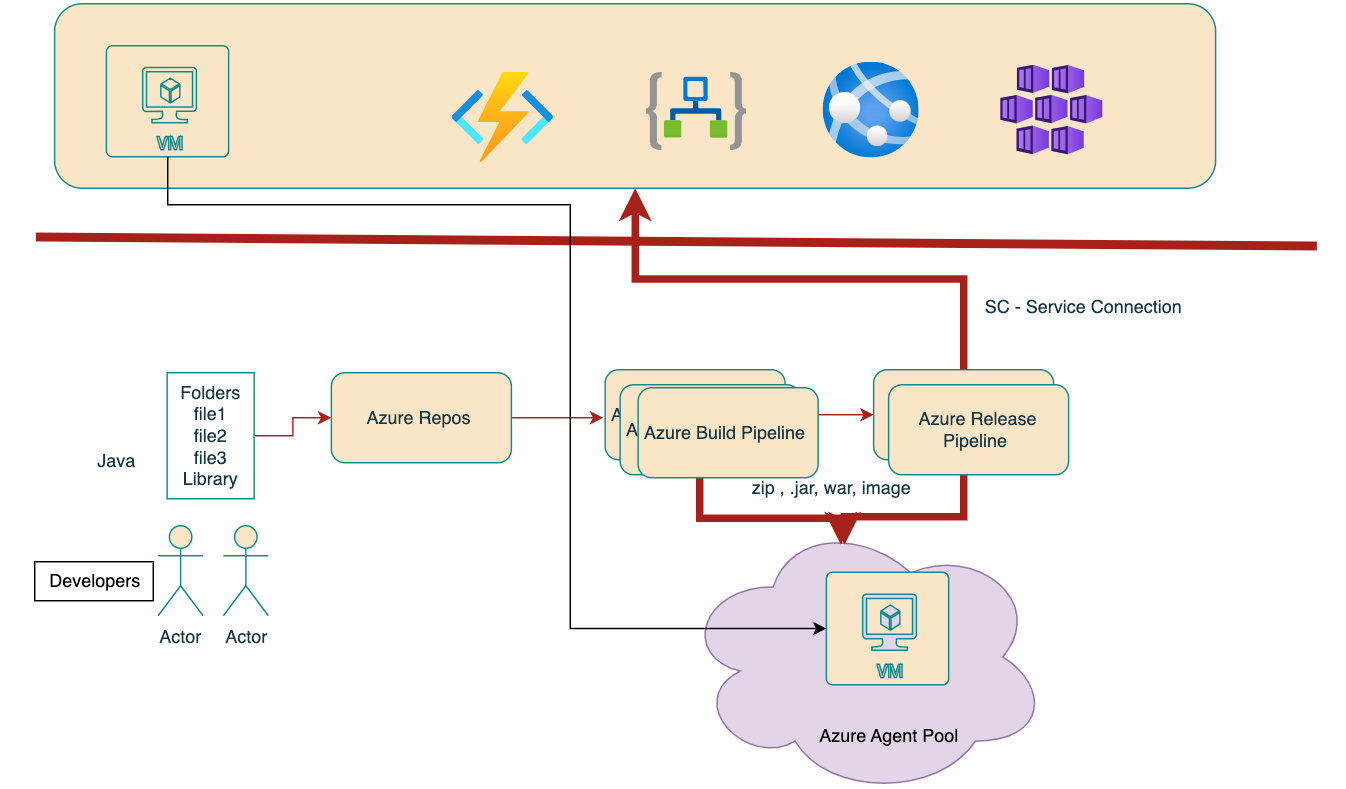
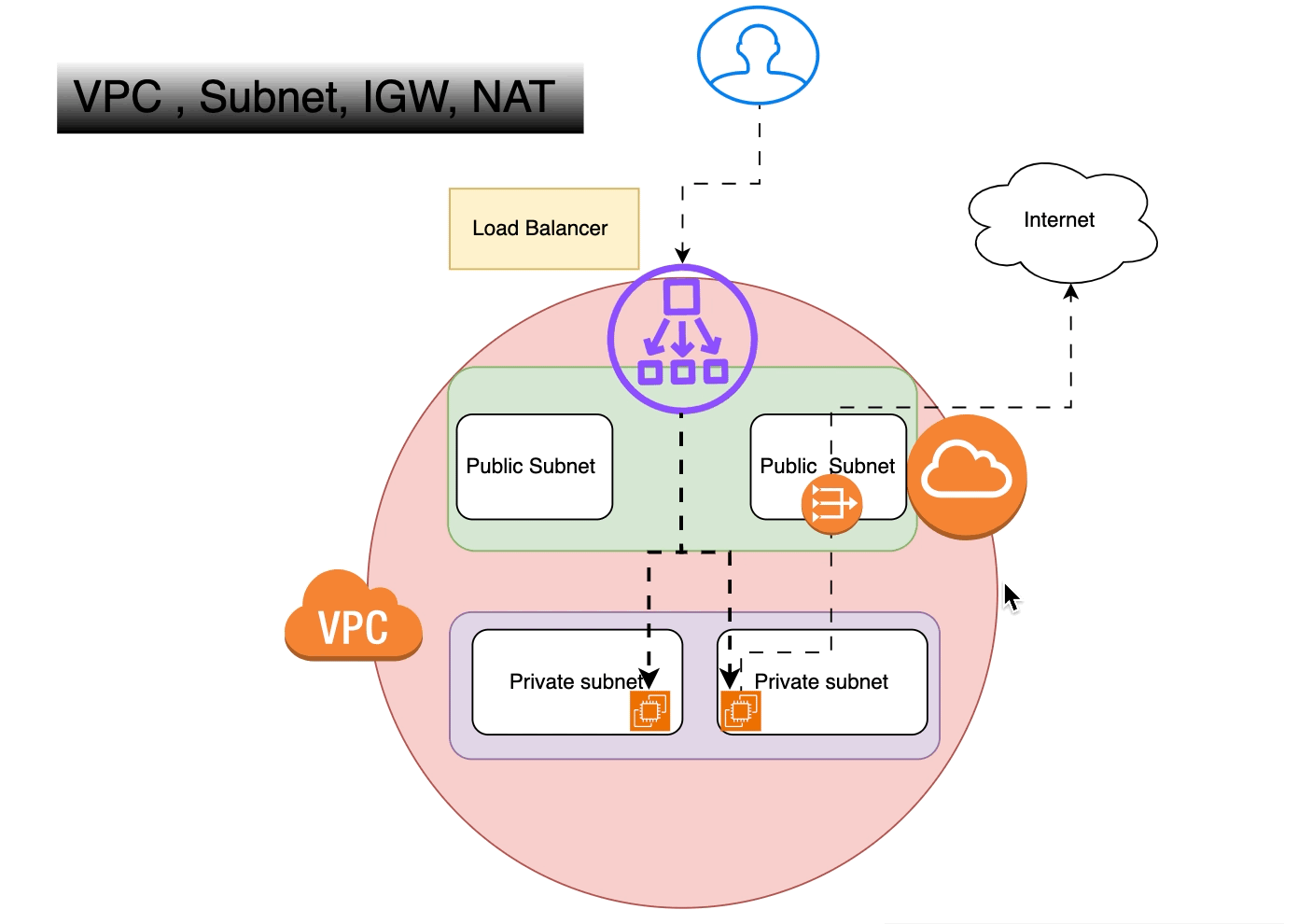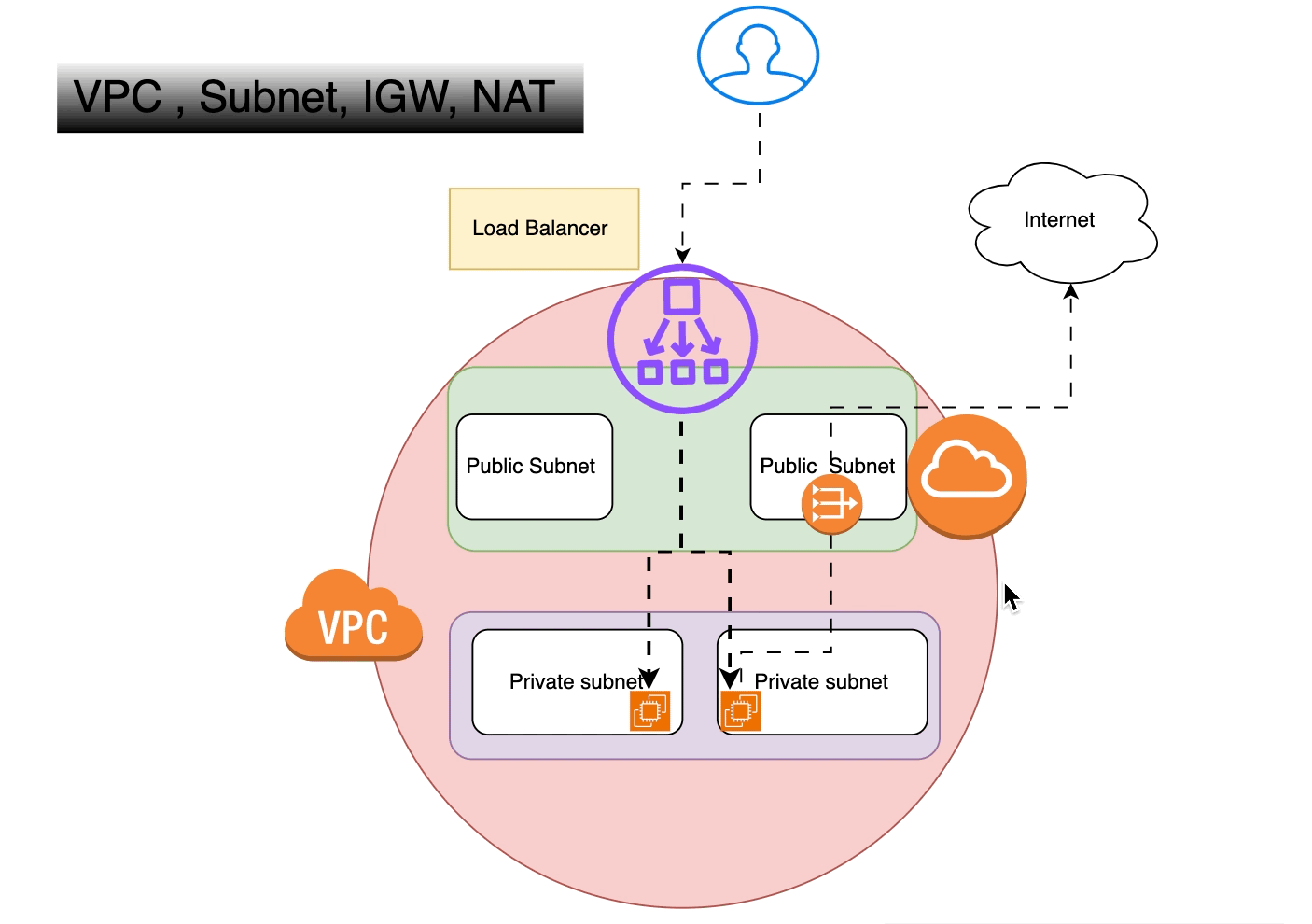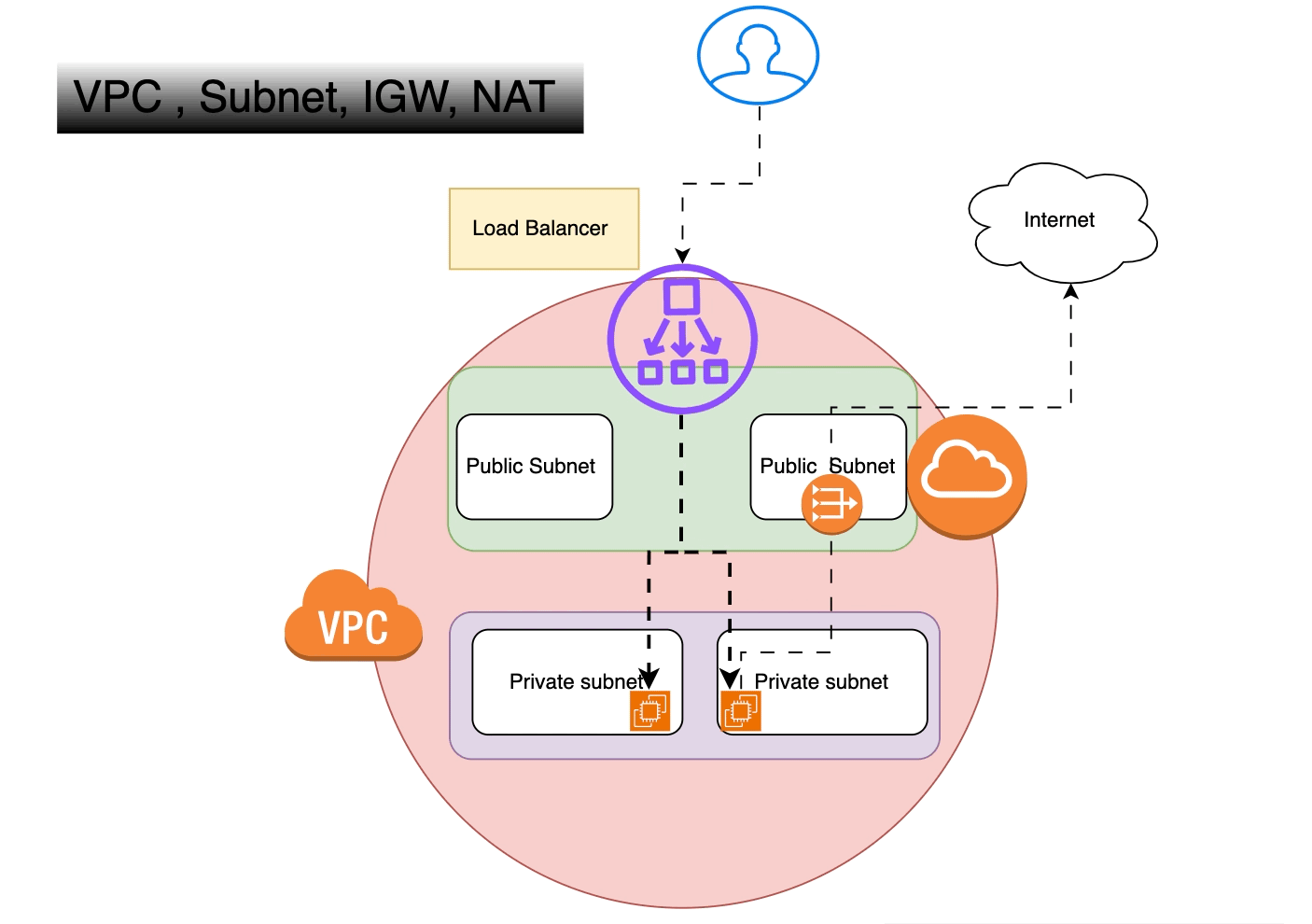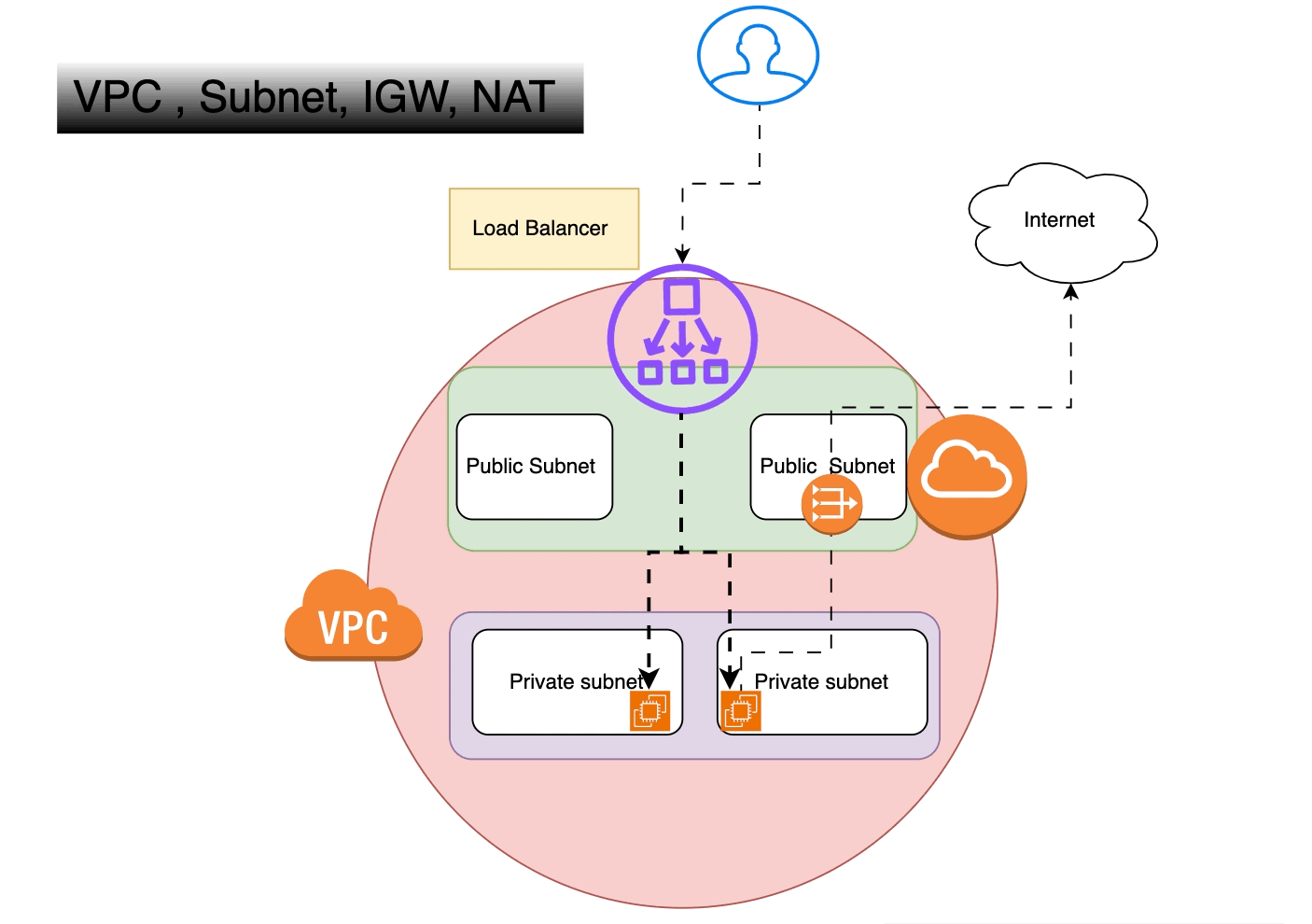
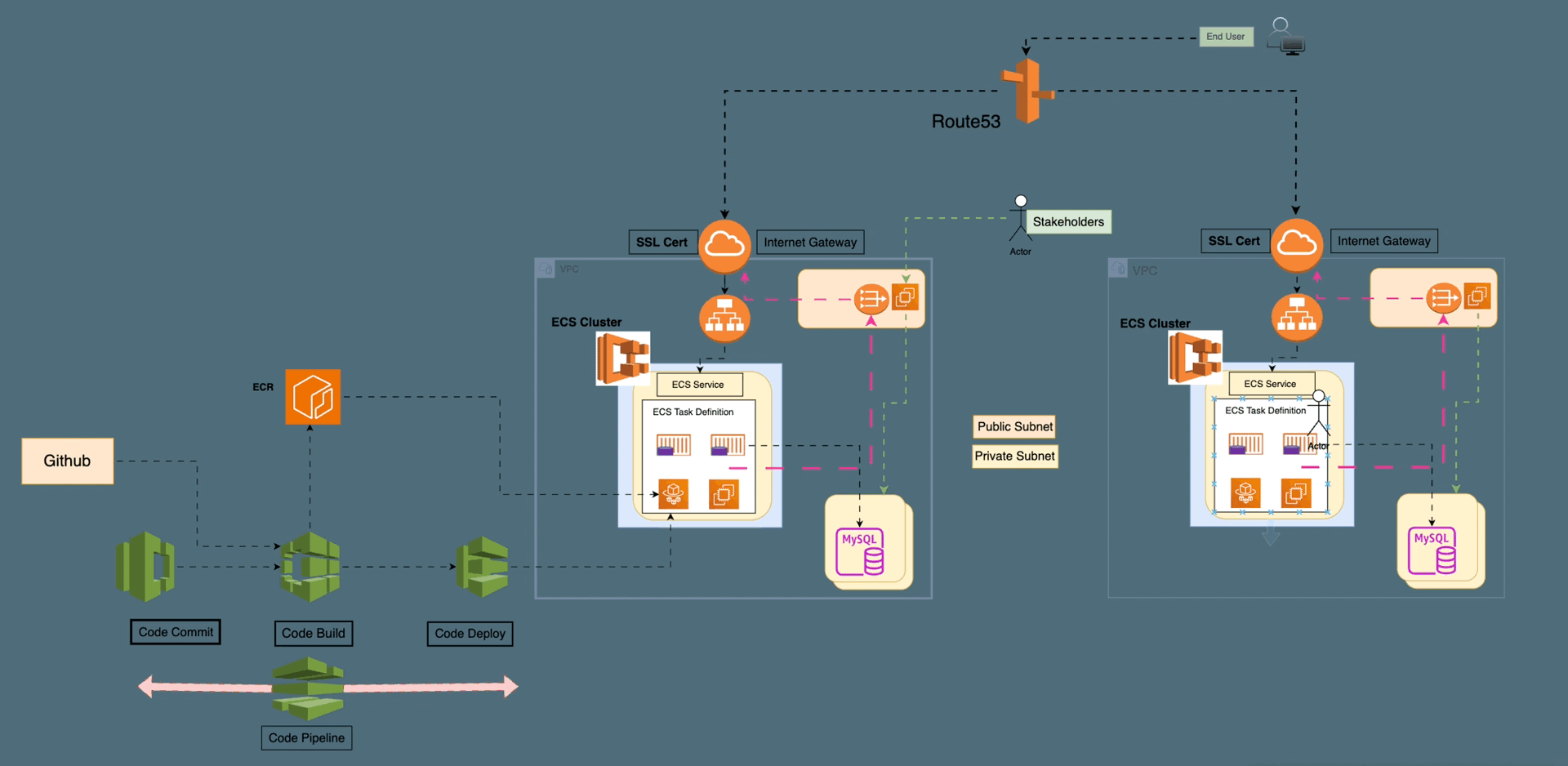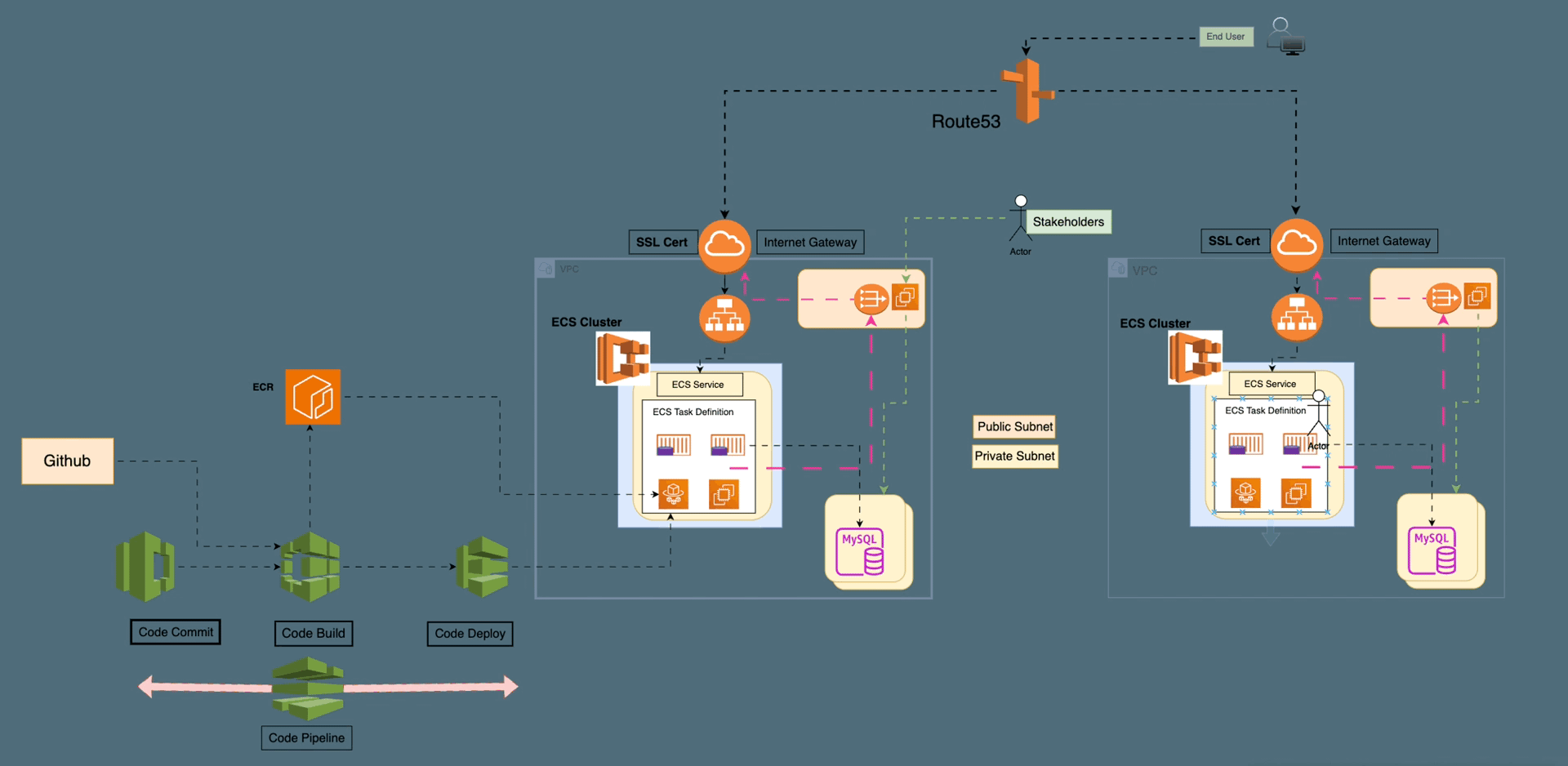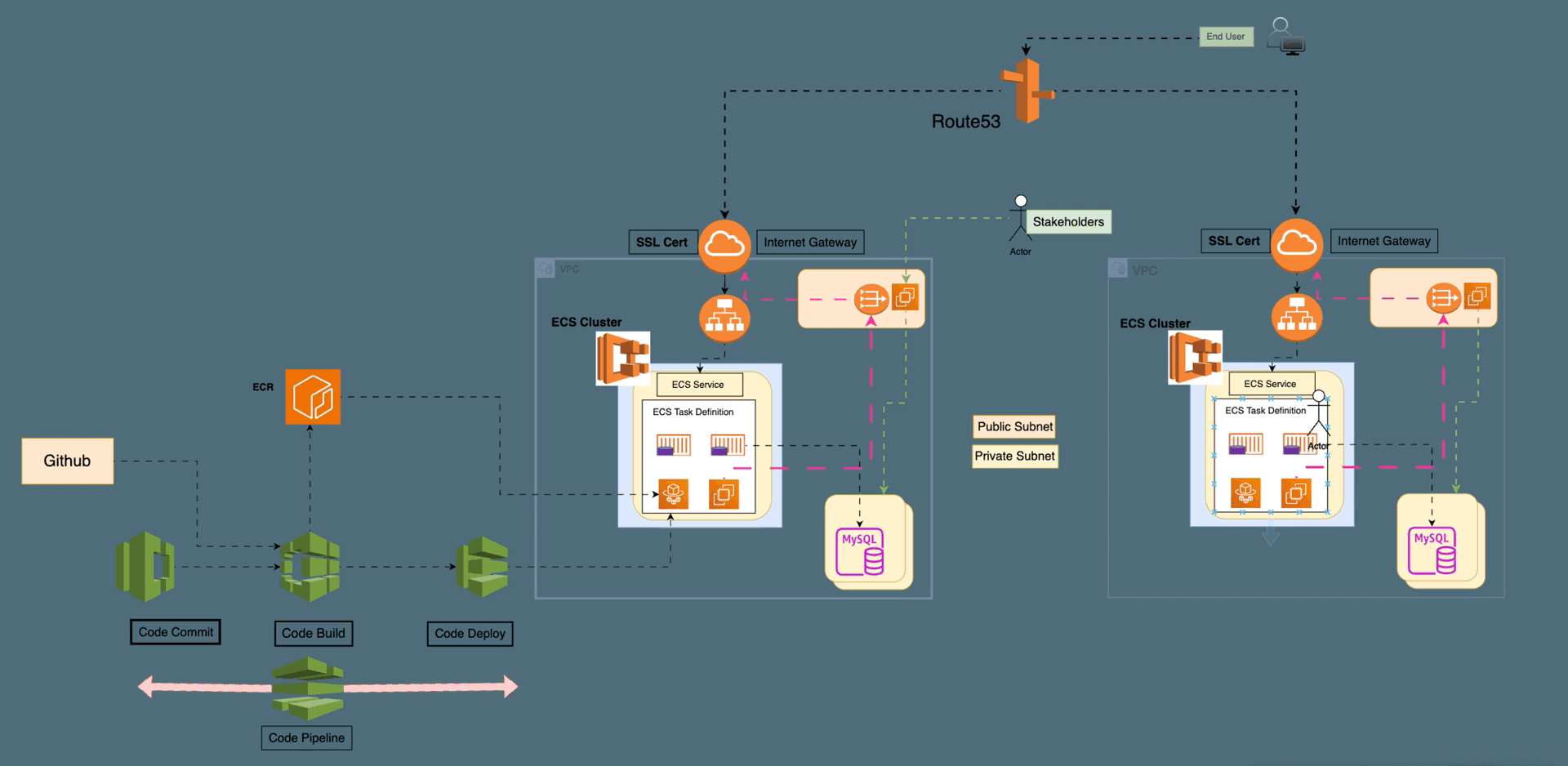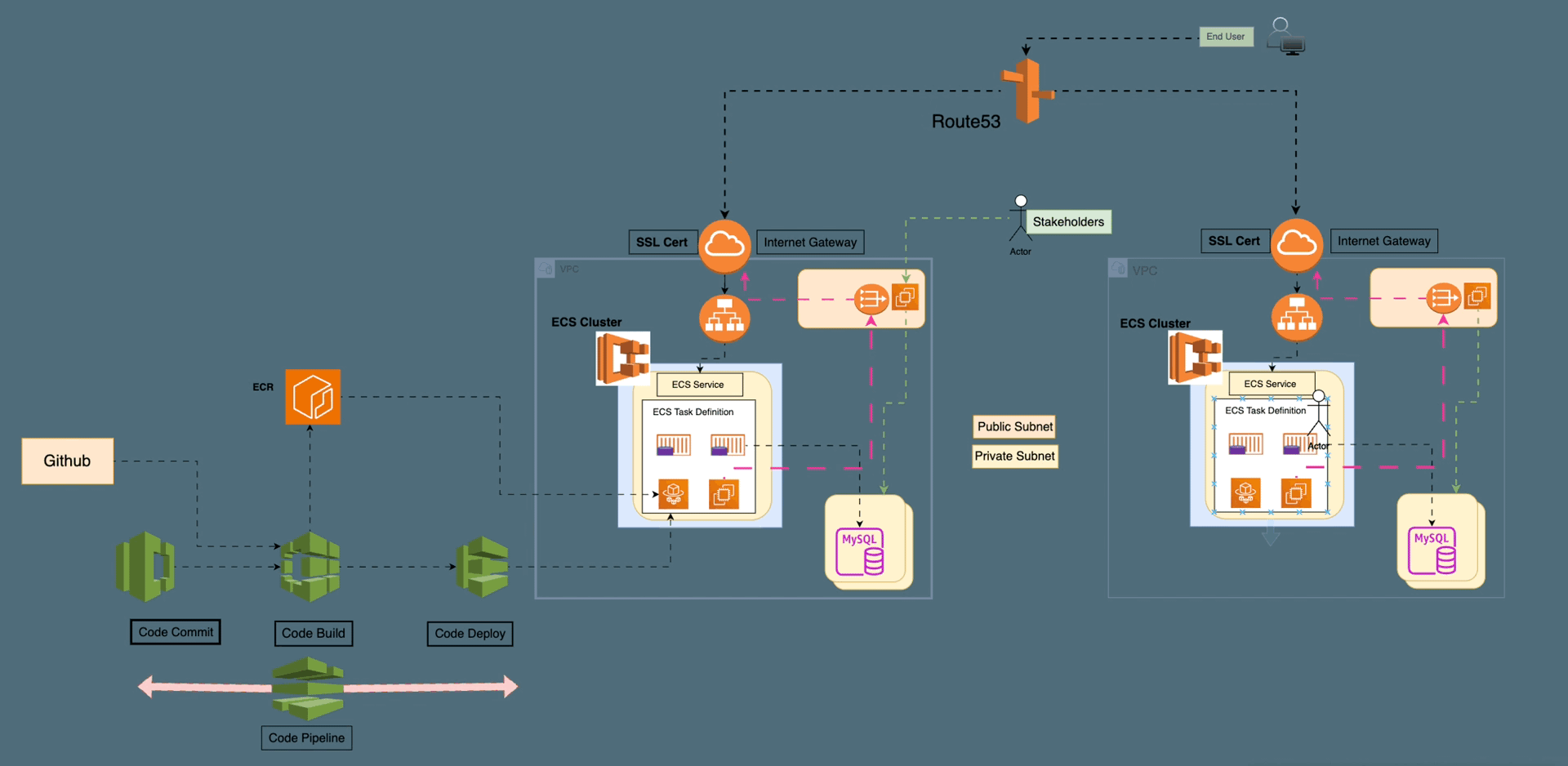
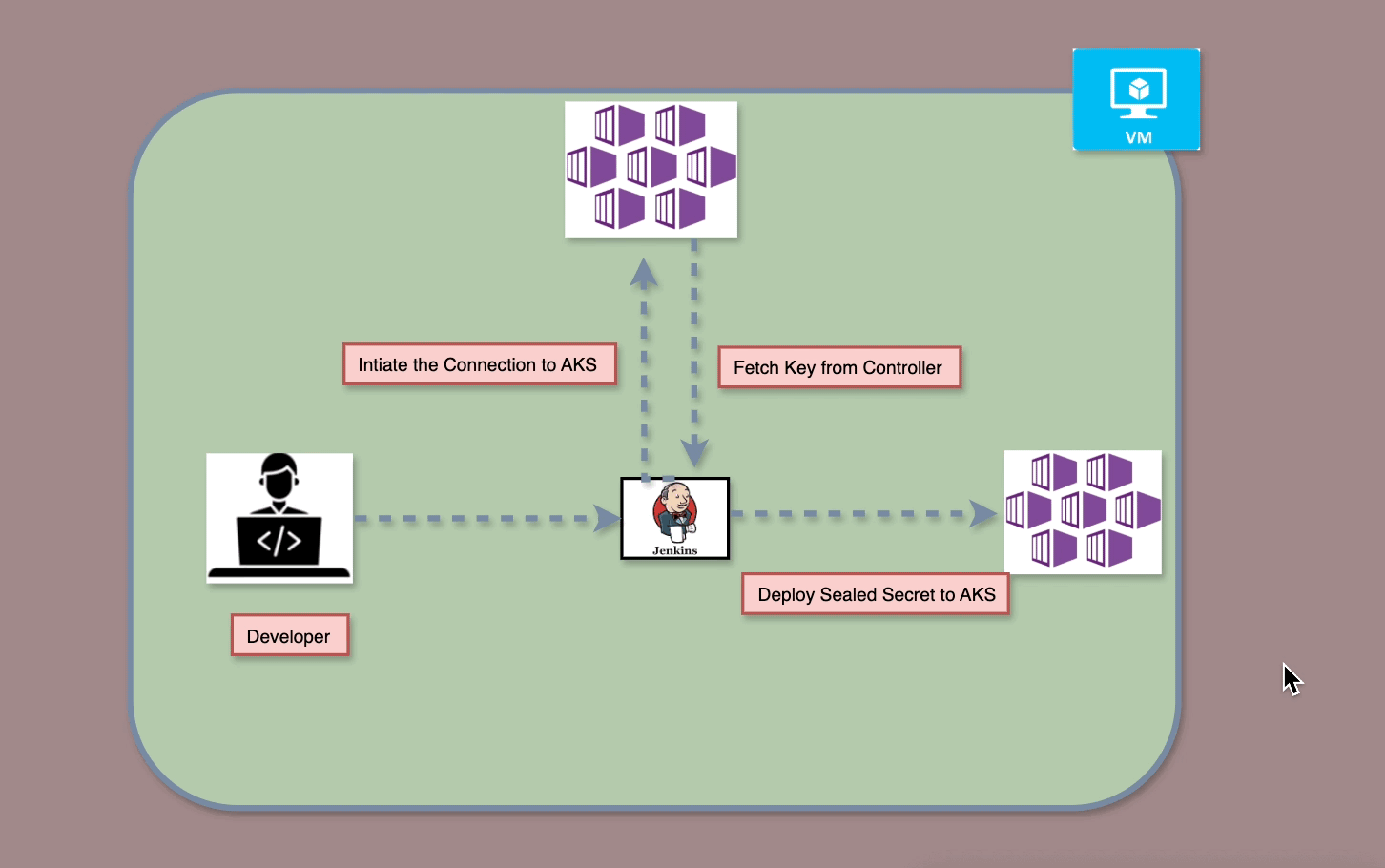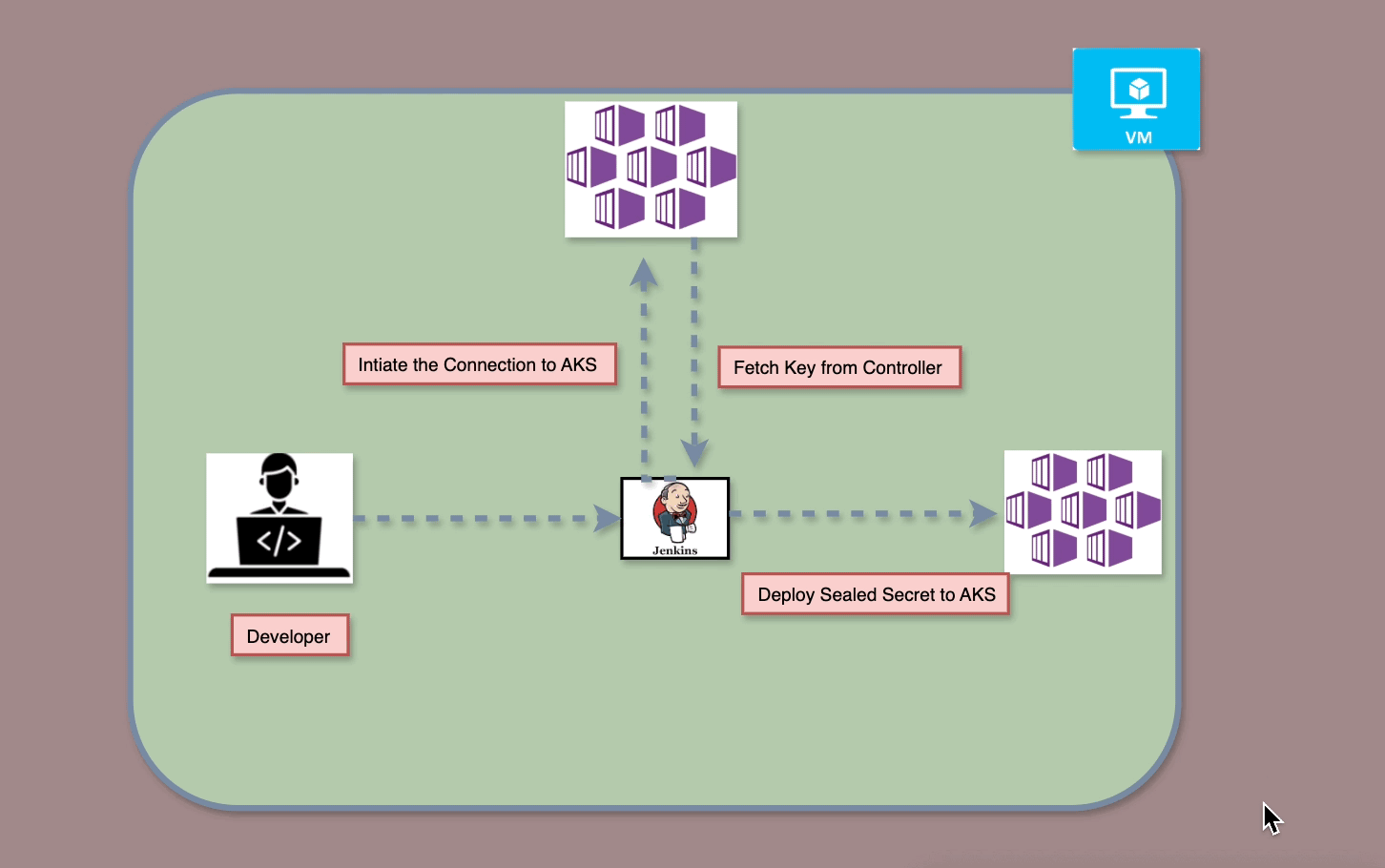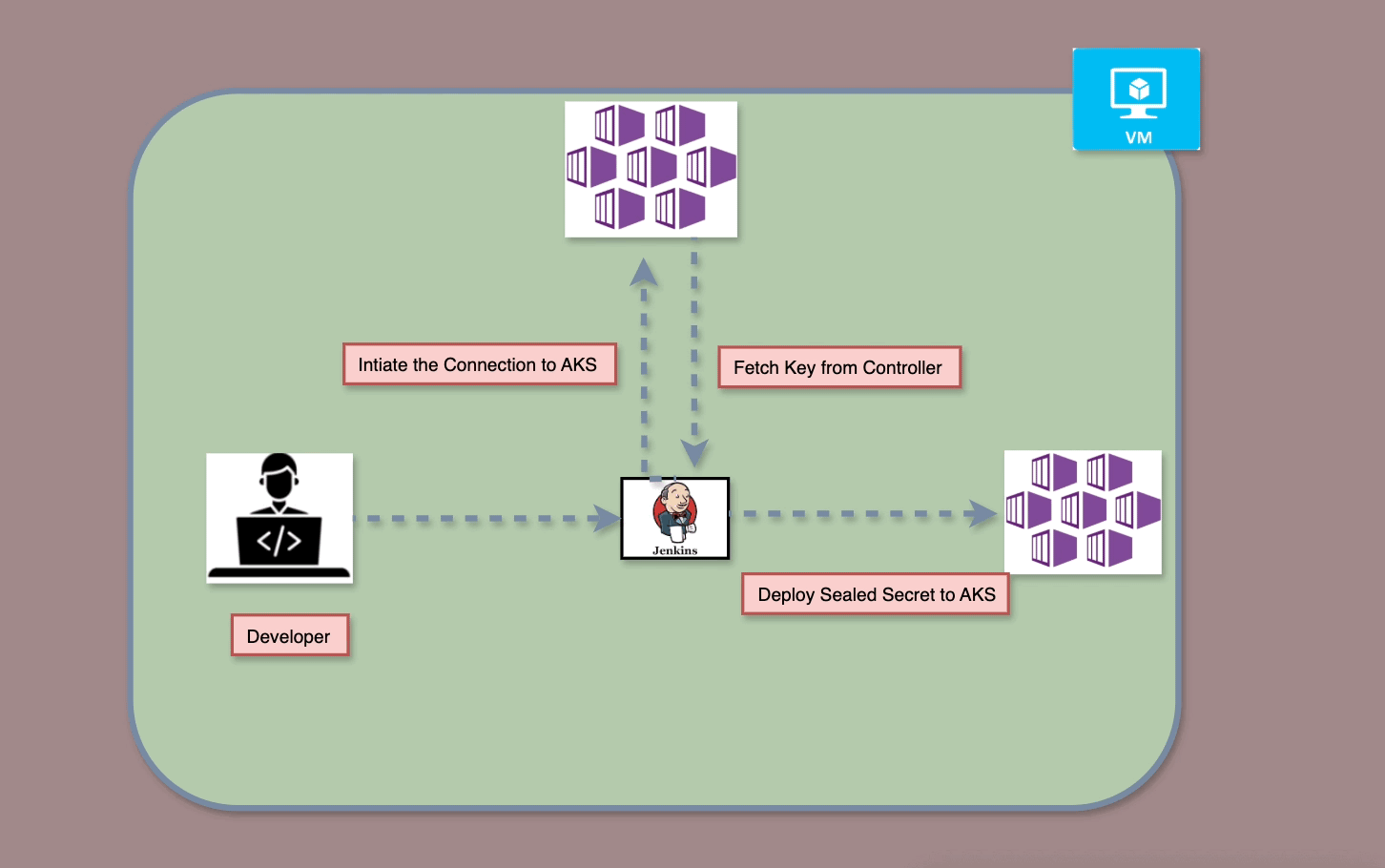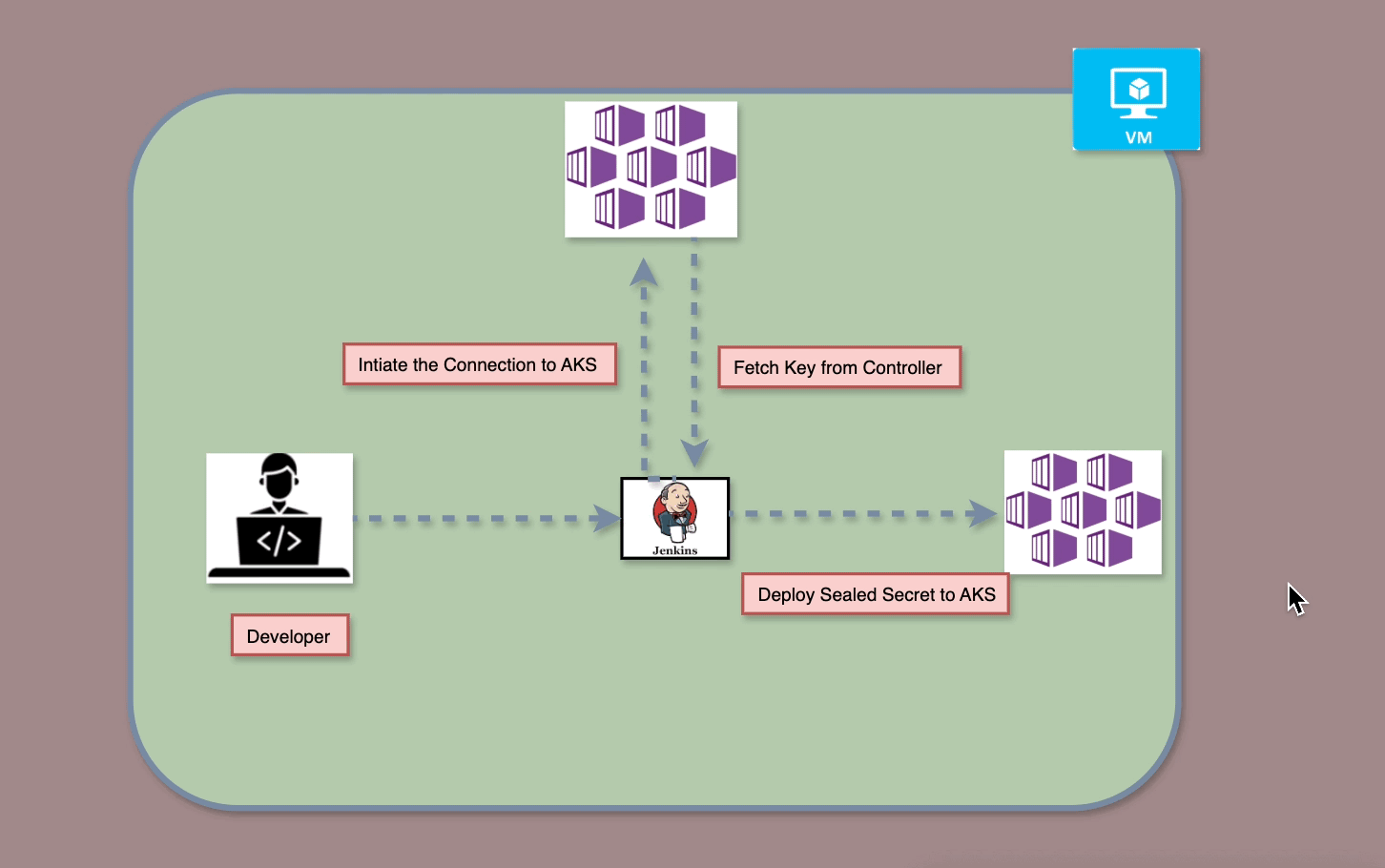
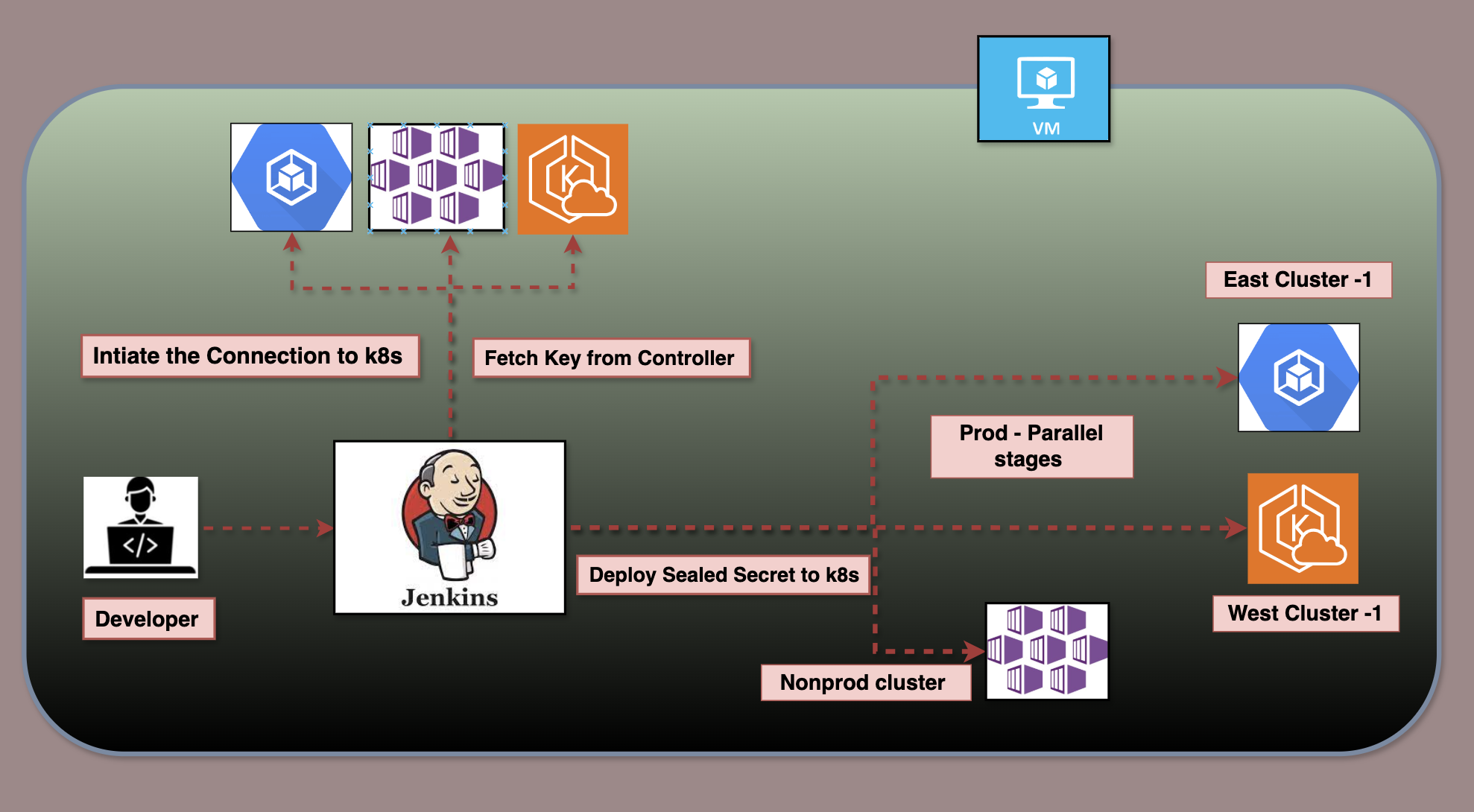
On-Premise vs. Cloud: Navigating the Landscape of Computing Solutions — Part1
On-Premise solutions offer control and security with high upfront costs, while Cloud Computing provides flexible, scalable resources on a pay-as-you-go model. Choosing between them depends on organizational needs and cost considerations.