Azure Kubernetes Service (AKS) allows you to deploy, manage, and scale containerized applications using Kubernetes. Azure Role-Based Access Control (RBAC) is a crucial feature for securing access to Azure resources, including AKS clusters. RBAC helps you control who can do what within your AKS environment.
The following steps will be pursued to accomplish the task:
- Generate a service principal.
- Include the service principal in the Active Directory (AD) Group.
- Grant access to the AD group on the Cluster.
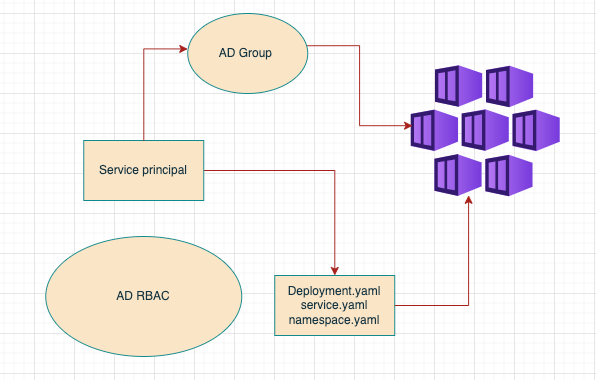
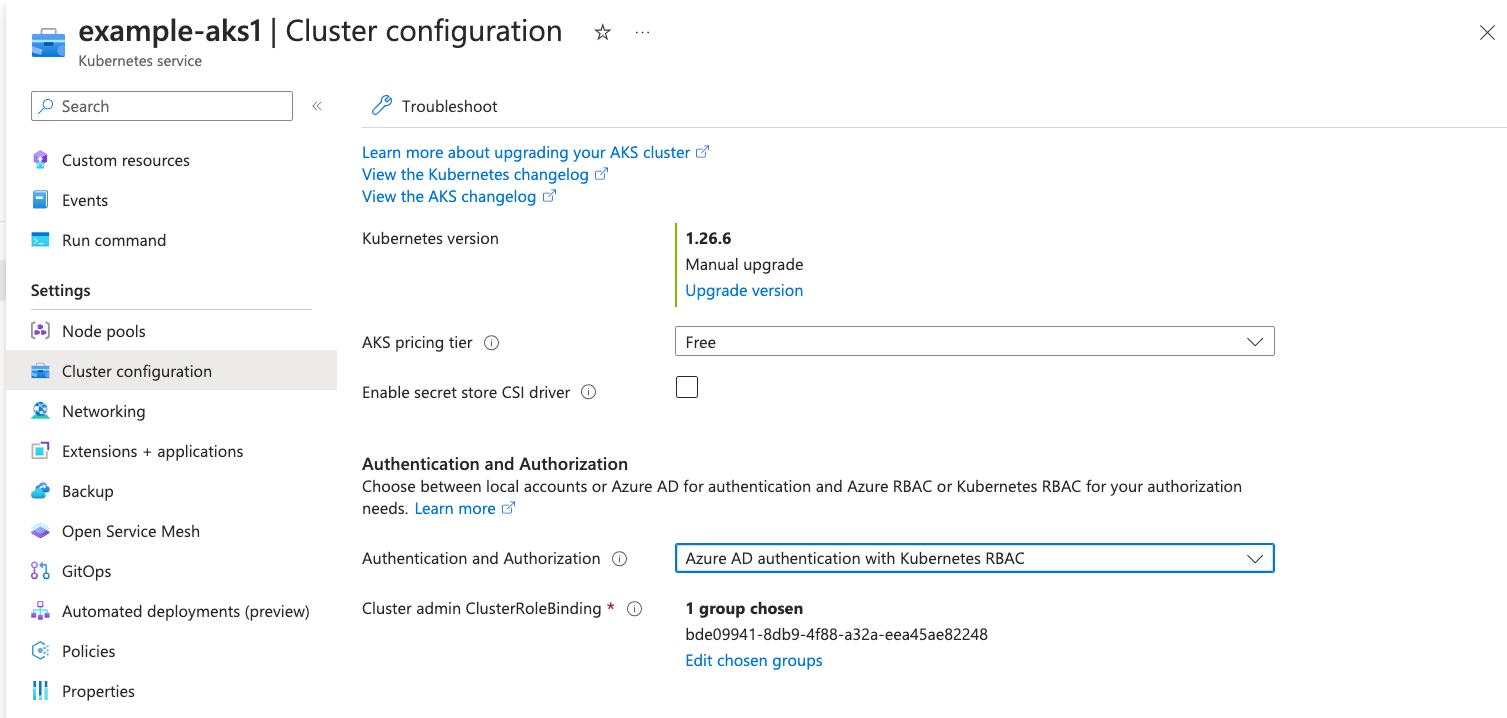
Here we provision the service principal and will create a azure ad group and we will add the service-principal to the AD group
service-principal.tf
resource "azuread_application" "example" {
display_name = "example"
}
resource "azuread_service_principal" "example" {
client_id = azuread_application.example.client_id
}
resource "azuread_service_principal_password" "example" {
service_principal_id = azuread_service_principal.example.object_id
}
resource "azuread_group" "example" {
display_name = "example"
owners = [data.azuread_client_config.current.object_id]
security_enabled = true
members = [
data.azuread_client_config.current.object_id,
azuread_service_principal.example.object_id,
]
}
main.tf
resource "azurerm_resource_group" "example" {
name = "example-resources"
location = "West Europe"
}
resource "azurerm_kubernetes_cluster" "example" {
name = "example-aks1"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
dns_prefix = "exampleaks1"
default_node_pool {
name = "default"
node_count = 1
vm_size = "Standard_D2_v2"
}
identity {
type = "SystemAssigned"
}
tags = {
Environment = "Production"
}
azure_active_directory_role_based_access_control {
managed = true
azure_rbac_enabled = true
admin_group_object_ids = [azuread_group.example.object_id]
tenant_id = data.azurerm_subscription.current.tenant_id
}
}
provider.tf
terraform {
required_version = ">= 1.2.2"
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = ">= 3.10.0"
}
}
}
provider "azurerm" {
features {}
}
data.tf
# reference to Azure Kubernetes Service AAD Server app in AAD
data "azuread_service_principal" "aks_aad_server" {
display_name = "Azure Kubernetes Service AAD Server"
}
# current subscription
data "azurerm_subscription" "current" {}
# current client
data "azuread_client_config" "current" {}
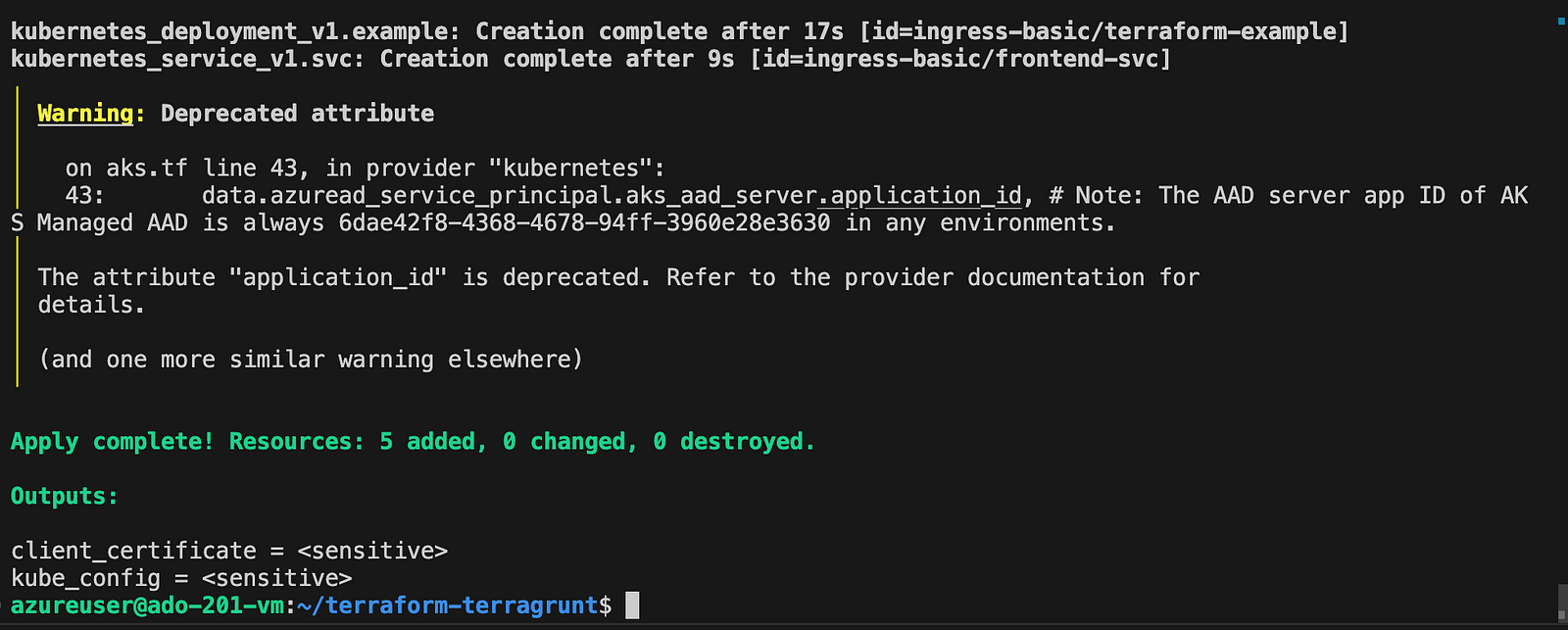
Result